The Latest
Filter by Topic
Filter by Type
Connesso Acquires McPherson Connected Systems
Connesso has officially announced the acquisition of McPherson Connected Systems (MCS). The transaction closed on Dec. 30, 2025…
News January 30Nice is Changing the Way ELAN Works in North America with Yubii OS
The new integration will allow integrators turn Nice’s control platform into a twin-OS offering benefits and integrations with…
News January 30Lightapalooza 2026 News & Coverage Hub
With Lightapalooza generating more and more news with each installment, this live blog page aims to keep CE…
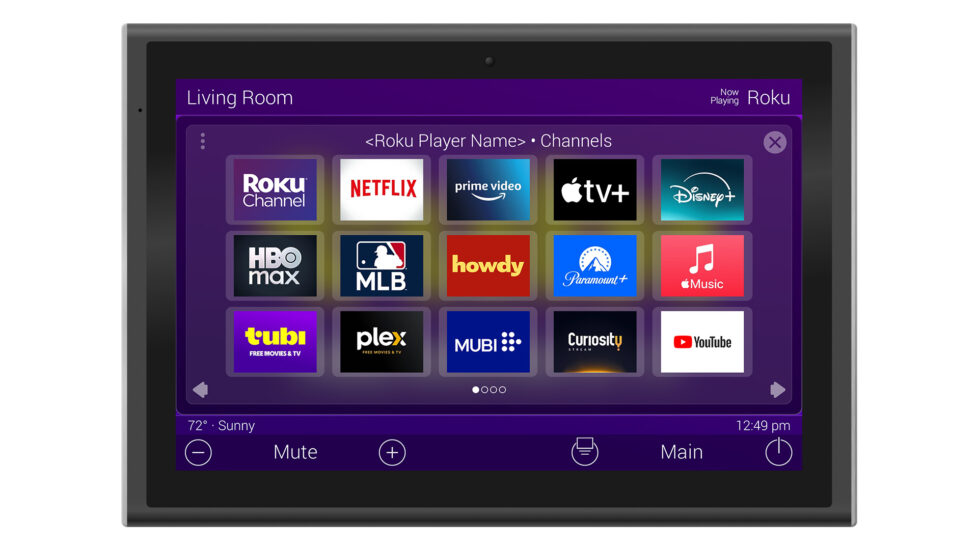
News January 30URC Introduces Roku Integration 3.0 for Total Control Systems
URC is expanding how Roku streaming devices and Roku TVs function within integrated residential systems.
News January 29Just Video Walls Retools Product Strategy with Agency-Style Reps
In its latest update, the company has announced it is making a full transition to developing agency-style rep…
News January 29ADI’s Luma X21 Refresh Aims to Modernize Its Residential Surveillance Portfolio
Updated 4-, 8- and 16-channel NVRs boost performance and add deeper Control4 and OvrC integrations.
News January 29Dreame Just Released Its Aura Mini-LED Series (as Well as Some Funky Robotics)
Announced during the company’s Beyond Smart event, the Aura series sits alongside weirder elements like an AI-powered laundry…
News January 29Level Up Automation Expands into Montana with New Missoula Location
Level Up Automation has expanded into Montana with the launch of a new Missoula location offering residential and…
News January 28Lightapalooza’s New Power Track Aims for a Comprehensive Look at Home Energy
Power and energy management continues to be a salient, if daunting, opportunity for integrators.
News January 28