When friends and family make their holiday wish lists, they provide parameters such as brand, model, size, shape, color, energy consumption, resolution, lumens, color temperature, and popularity.
Never do Johnny and Susie demand that their IoT and other network-connected gifts be immune to cybersecurity attacks.
Thankfully, the snot-nosed ingrates have a self-appointed savior in Mozilla, the Web-technology pioneer behind Firefox. The company has published its second annual list of naughty and nice products for the holiday season, judging their worthiness by the secrets they keep and the cyberthreats they suppress.
The so-called *Privacy Not Included roster applies Mozilla’s 5-point minimum security guidelines to 70 connected products across six categories, including smart-home, entertainment and wearables.
The media streamers, voice assistants, pet feeders, smart thermostats, Fitbits, gaming consoles and drones that don’t meet Mozilla’s minimum standards – or that generally creep consumers out – get dinged on the Creep-O-Meter.
Mozilla itself makes no judgment on the creepiness of any given product. It simply presents the objective data on a product's security-related features, and lets the rest of the world assign an ick factor.
The Creep-O-Meter is a silly gimmick, but the whole Mozilla exercise is a useful one, and potentially a type of service that integrators could provide, especially during the holidays, when connected gear rains down on careless, digitally naive consumers who are grateful the manufacturer randomly assigned them an easy p-a-s-s-w-o-r-d to remember.
Mozilla’s digital security standards include the following, with some caveats and additional guidelines:
Minimum Security Standards
- Encrypted communications
The product must use encryption for all of its network communications functions and capabilities. This ensures that all communications are not eavesdropped or modified in transit.- Security updates
The product must support automatic updates for a reasonable period after sale, and be enabled by default. This ensures that when a vulnerability is known, the vendor can make security updates available for consumers, which are verified (using some form of cryptography) and then installed seamlessly. Updates must not make the product unavailable for an extended period.- Strong passwords
If the product uses passwords for remote authentication, it must require that strong passwords are used, including having password strength requirements. Any non unique default passwords must also be reset as part of the device’s initial setup. This helps protect the device from vulnerability to guessable password attacks, which could result in device compromise.- Vulnerability management
The vendor must have a system in place to manage vulnerabilities in the product. This must also include a point of contact for reporting vulnerabilities or an equivalent bug bounty program. This ensures that vendors are actively managing vulnerabilities throughout the product’s lifecycle.- Privacy Practices
The product must have a privacy policy that is easily accessible, written in language that is easily understood and appropriate for the person using the device or service. Users should at minimum be notified about substantive changes to the policy. If data is being collected, transmitted or shared for marketing purposes, that should be clear to users and, as in line with GDPR, there should be a way to opt-out of such practices. Users should also have a way to delete their data and account. Also in line with the EU’s General Data Protection Regulation (GDPR), this should include a policy setting standard retention periods wherever possible.
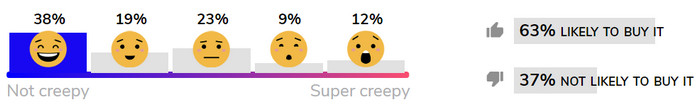
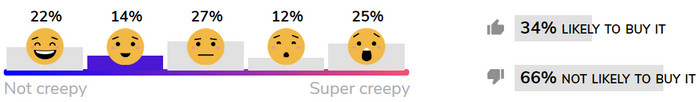
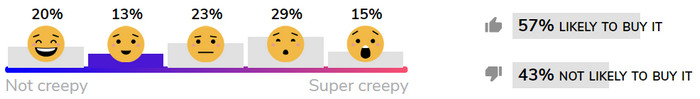
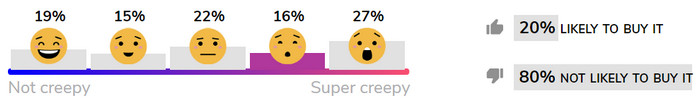
Some Creep-o-Meter Standings
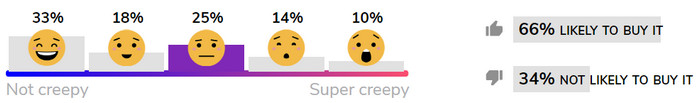
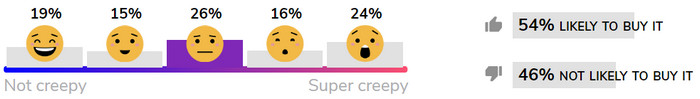
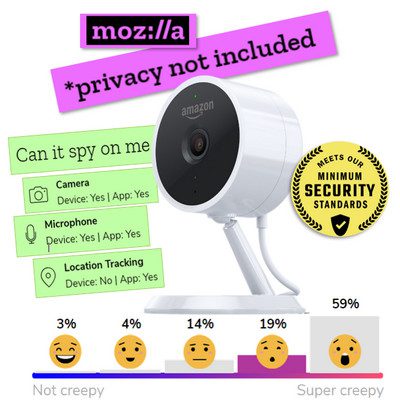
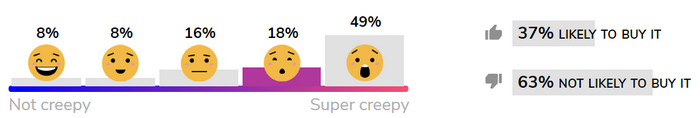
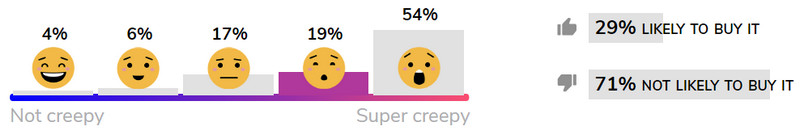
In early rounds of consumer evaluations, there seems to be no discernible pattern on the level of ick consumers assign to certain products. Why would Amazon Echo, for example, seem creepier than Google Home (below)?

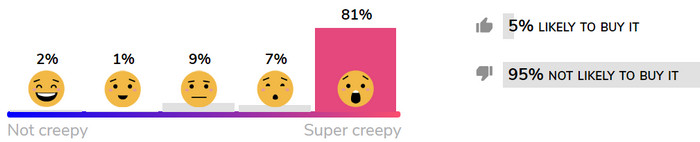
Some of the products are icky at first sight, even without reviewing Mozilla's objective privacy and data-security criteria. The Fredi baby cam? The kid in the app looks horrified — probably by the sight of the Darth Vader plastic puppy on the dresser, pretending to be an adorable plaything. Creepy for sure, according to me … and 81% of early voters.
In my view, the Parker Teddy Bear seems straight out of The Miscreant's Handbook, but only 27% of early reviewers ranked it super-creepy. Granted, the thing doesn't connect to the network.
In fact, it doesn't do much of anything, so it wouldn't be subject to IoT breaches. But in the hands of an ill-intentioned visitor, the floppy pile of fluff could be hacked to house a discreet camera or remote-controllable fart machine.
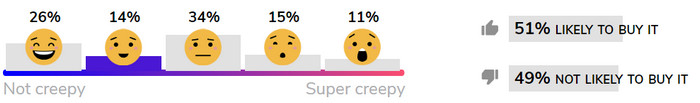
Here’s how some of the evaluated products are faring on Mozilla’s crowd-sourced Creep-o-Meter scale: